how can cyber attack virus causes data loss
Ransomware is not the only concern. The Brain boot sector virus aka Pakistani flu the first IBM PCcompatible virus is released and causes an epidemic.
Cybersecurity Statistics For 2021 Packetlabs
The codes malicious activity could damage the local file system steal data interrupt services download additional malware or any other actions coded into the program by the malware author.

. An SQL structured language query injection is a type of cyber-attack used to take control of and steal data from a database. Corrupt or delete data on a computer. Phishing is a popular cyber-attack since adversaries usually do not require sophisticated hacking tools or expertise.
How Do Data Breaches Occur. An astonishing data University of Maryland reveals that hackers attack every 39 seconds which makes Cyber Security a major challenge in the contemporary world. Security data of an individual is easy to manage but when data gets bigger it becomes hard to secure it from external or cyber-attacks.
Over the next sections well take a look at other common attack vectors. After this Virus causes some psychological effects of the user they put that unwanted thing in their computer through the illness. Phishing attacks can result in adverse results.
Losing files and documents often has a lasting impact on your companys financial health. Cyber threats include computer viruses data breaches Denial of Service DoS attacks and other attack vectors. The name refers to a vendor or organisation having no time to fix the vulnerability prior to attack.
But in circumstances like data infringement it takes time to retrieve the funds which is very worrying for. In this post we will discuss on different types of security threats to organizations which are as follows. It propagated via infected email attachments and via an existing.
Cryptojacking attacks made a comeback in 2020 after seeing huge declines in the latter half of 2019. Viruses physical damage or formatting errors can render data unreadable by both humans and software. This can be done by accessing a computer or network to steal local files or by bypassing network security remotely.
Interception attacks allow unauthorized users to access our data applications or environments and are primarily an attack against confidentiality. A Trojan can launch an attack on a system and can establish a backdoor which attackers can use. Physical tampering may result into misleading data in cyber-physical components.
Loss to Customers. It has become the talk of every town with almost 1378509261 data records breached since 2016In the following sections we shall be shedding light on some of the common types of data breach and the major causes of a data breach. Cyber threats also refer to the possibility of a successful cyber attack that aims to gain unauthorized access damage.
Other common cyber attack tactics. The attack utilized a trojan that targeted computers running Microsoft Windows and was believed to have first been posted to the Internet on 5 September 2013. Ransomwareprevents access to the data of the victim and threatens to delete or publish it unless a ransom is paid.
A virus needs user interaction to trigger it. This gives them access to the sensitive information contained in the database. A virus is a software program that can spread from one computer to another computer or one network to another network without the users knowledge and performs malicious attacks.
When a bank confronts a cyber attack it not only affects the banks status but also causes loss to its customers assets. Cybercriminals exploit vulnerabilities in data-driven applications to insert malicious code into a databased via a malicious SQL statement. Data loss occurs when data is accidentally deleted or something causes data to become corrupted.
A phishing attack occurs when a hacker posing as a legitimate trusted individual or organization tricks a person into opening a malicious link attachment or email. In such a CPS type an attack can lead to loss of life or to chronic deadly diseases with significant damage to the environment such as fire. It is often difficult or impossible to safeguard a system from data breaches that involve complex technologies.
Interception might take the form of unauthorized file viewing or copying eavesdropping on phone conversations or reading e-mail and can be conducted against data at rest or in motion. Favored cyber attack tactics include cryptojacking and encrypted communication. Take a look at some of the major causes of cyber crimes that you must be acquainted with.
This leads to a buffer overflow and causes the cyber-physical system to crash. Three-quarters of businesses have experienced data loss from a cloud service more than once. Data breaches today tend to impact millions of consumers in just one attack on a company.
This could come in the form of a direct hacking attempt a phishing attempt or some other version of spam meant to infect your computer with harmful software known as malware. Types of Cyber Security Cyber Security is just an umbrella term that comprises various layers of security undertakings to secure data from cyber threats. The cyber security of a company can be compromised in many ways when it comes to software and computer administration.
Data Breach has created a new uproar in the world of cybersecurity. A computer virus is a malicious application or authored code used to perform destructive activity on a device or local network. Normally when a user loses money due to card fraud it can be retrieved from the bank.
It was created in Lahore Pakistan by 19-year-old Basit Farooq Alvi and. There is a cyber-attack once every 39 seconds According to a study from the University of Maryland a typical computer is attacked in one way or another every 39 seconds. Types of cybercrimes include pornography cyber fraud defamation cyberstalking harassment IPR theft data hostage money laundering phishing email bombing cyber warfare illegal FTF.
Cyber-dependent and cyber-enabled crimes A cyber-dependent crime is an offence that can only be committed using a computer computer networks or other form of information communications technology ICT McGuire and Dowling 2013aCyber-enabled crimes are traditional crimes. Types of Security Threats to Organizations. You need to hire professional cybersecurity service to provide to fully protect your companys or business data from external access of cyber attack.
Security can only be compromised when the system is easy to access for hackers. As such software and computer administration is a great source of cyber security research topics. A data breach occurs when a cybercriminal infiltrates a data source and extracts confidential information.
The CryptoLocker ransomware attack was a cyberattack using the CryptoLocker ransomware that occurred from 5 September 2013 to late May 2014. A cyber or cybersecurity threat is a malicious act that seeks to damage data steal data or disrupt digital life in general. The field is becoming increasingly significant due to the continuously.
The process of making a copy of data in an archive which can be used to reconstruct the original data in the event of a loss corruption or disaster. Cyber attacks are more likely to bring down F-35 jets than missiles. Phishing is one of the top causes of data breaches followed by the use of stolen credentials and ransomware.
Trojan virustricks a user into thinking it is a harmless file. The CPS guidelines categorise cyber-crime into two broad categories. Computer security cybersecurity or information technology security IT security is the protection of computer systems and networks from information disclosure theft of or damage to their hardware software or electronic data as well as from the disruption or misdirection of the services they provide.

How To Survive This Era Of Cyber Attacks Daily Infographic Cyber Attack Infographic Cyber Threat

Cyber Security Checklist Cyber Security Cyber Security Awareness Online Security

7 Types Of Cyber Security Threats
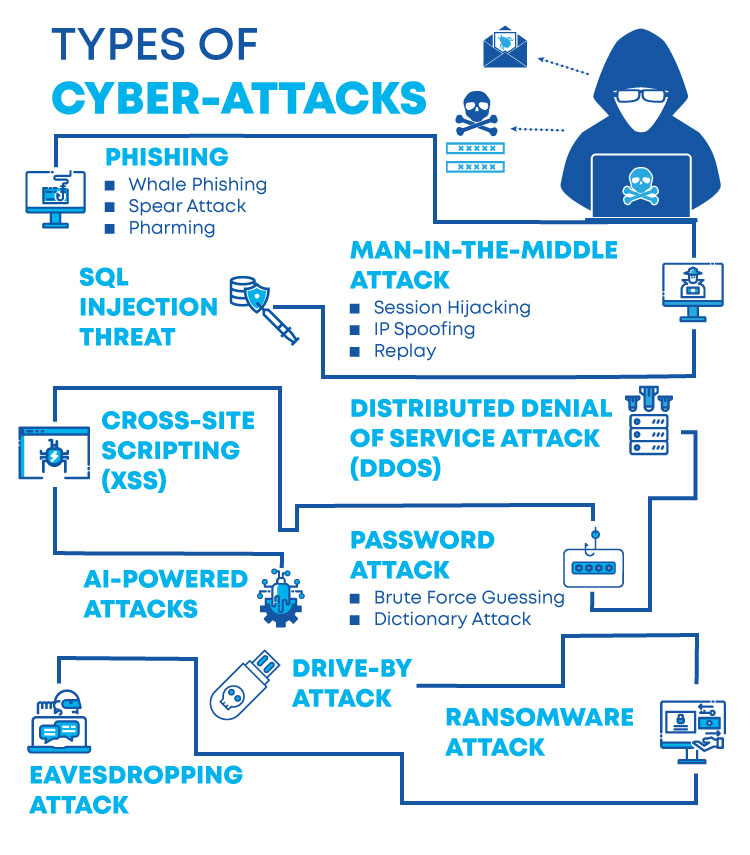
Types Of Cybersecurity Attacks And How To Prevent Them

Cyber Attacks Tips For Protecting Your Organisation Ecu Online

6 Ways To Reduce The Risk Of Cyber Attacks

Types Of Cybersecurity Attacks And How To Prevent Them

5 Steps To Shield Your Organization From Cyber Threats Cyber Threat Cyber Security Threat

5 Best Practices To Prevent Data Breaches Posts By Ctg Tech Data Breach Managed It Services Security Solutions
0 Response to "how can cyber attack virus causes data loss"
Post a Comment